by Josef Weiss
December 22, 2020
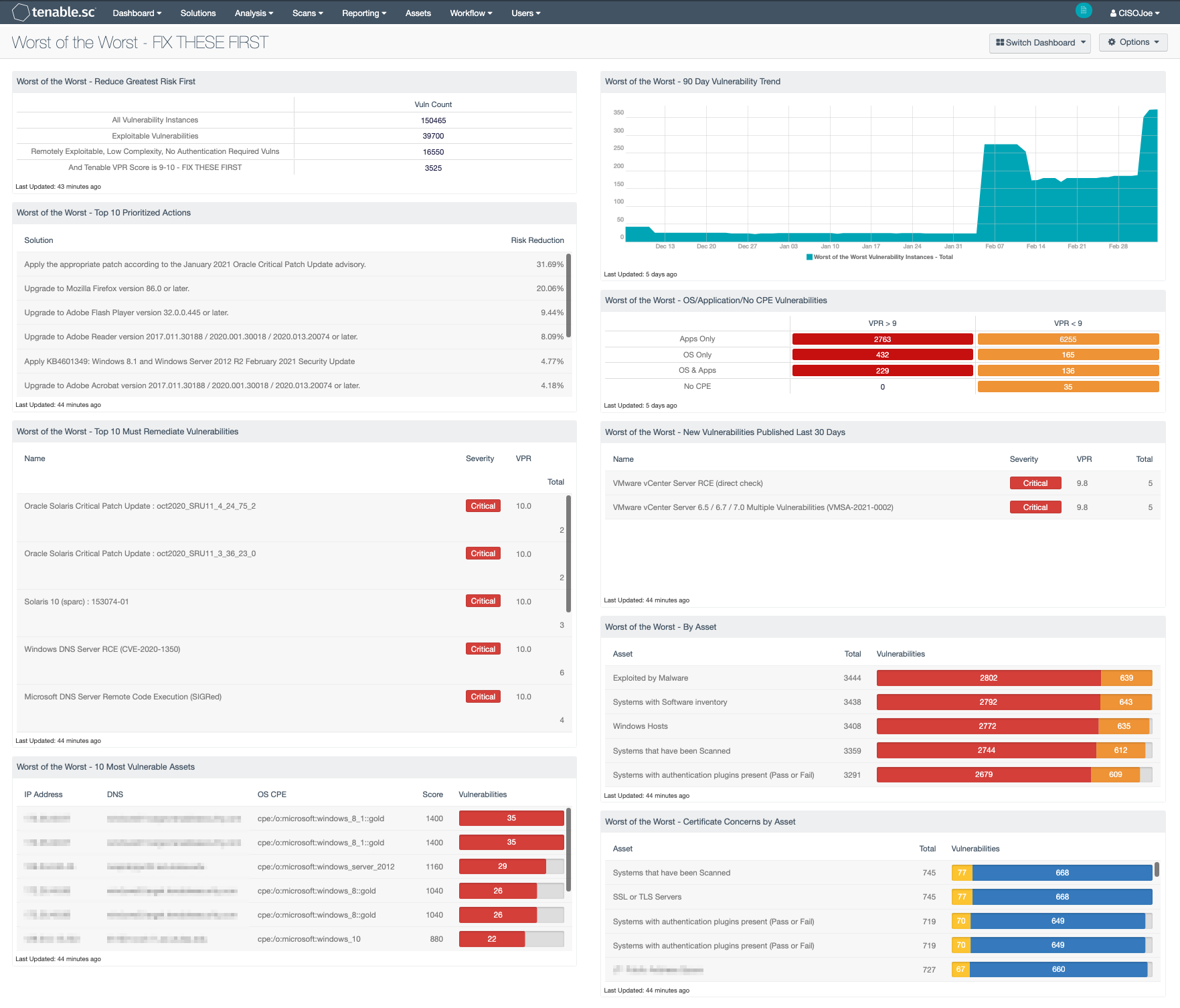
This dashboard enables customers building or strengthening a vulnerability management program to better visualize the modern attack surface. Information presented focuses on the vulnerabilities that organizations should prioritize and mitigate first, by leveraging the Vulnerability Priority Rating (VPR). The VPR score is an output of Predictive Prioritization, which allows organizations to focus on what matters first by combining research insights, threat intelligence, and vulnerability rating to reduce noise. Effective vulnerability remediation becomes easier as vulnerabilities, that will cause the most significant impact, float to the top. VPR ratings can change over time, as threat intelligence information changes. Again, allowing teams to focus on what is important right now
The prioritized data establishes a measurable reference point used by IT administrators to create actionable mitigation tasks based on VPR, and improved the risk reduction timelines. The dashboard is laid out to provide the details on the Top 10 prioritized actions and most urgent vulnerabilities, in a variety of easy to digest formats without being overwhelming to the viewer. Designed with the principles of Cyber Exposure Management in mind, the full series is tailored to guide Executives, Managers and Operations Teams to see, predict, and act to reduce risk across their entire attack surface. Administrators within these teams can expertly track risk and vulnerabilities within their area of expertise, remediate the identified risk, track progress, and measure success against their own team charter and SLAs.
When not using VPR as a filter to focus on the most significant concerns, noise increases and the large number of critical and high vulnerabilities, as determined most often by Common Vulnerability Scoring System (CVSS) rating, become cumbersome and difficult to sort. Teams begin to lose focus and find difficulty in identifying a starting point to prioritize remediation efforts as they try to patch everything on the radar.
Through a sea of vulnerabilities, this dashboard narrows down those findings to those which are most important, via a progressive series of simple filters:
- First, list the total vulnerability count.
- Second, apply an Exploit Available filter.
- Third, apply a filter that narrows things down to those exploitable vulnerabilities that are Remotely Exploitable, Low Complexity, and where No Authentication is Required.
- Finally, a VPR filter breaks out an even smaller subset of the highest risk vulnerabilities in your environment that are most likely to be exploited and have the greatest impact in the next 30 days.
These worst-of-the-worst vulnerabilities are what your organization needs to focus on first.
Many organizations have created specialized Remediation Teams. These teams often have operations-centric dashboards that focus on detailed information, relevant to the teams’ own assets; or area of operational focus, such as Windows, Linux, databases, or network infrastructure. The components do not require specific assets to be loaded prior to use, however, teams that do focus on a specific group of assets, can benefit from customizing filters around those assets for the individual components. Additionally, the management/leadership of these lines of business, who are responsible for remediating risk on their own assets, will benefit from the information presented. Management needs to see the work their team performs, as well as measure progress and success against their workload.
This dashboard is available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards, and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Threat Detection and Vulnerability Assessments.
The dashboard requirements are:
- Tenable.sc 5.15.0
- Nessus 8.11.1
Tenable.sc Continuous View (CV) is the market-defining On-Prem Cyber Exposure Platform. Tenable.sc CV provides the ability to continuously Assess an organization’s adherence to best practice configuration baselines. Tenable.sc provides customers with a complete Cyber Exposure platform for completing effective cybersecurity practices
Components
- Worst of the Worst - Reduce Greatest Risk First - This matrix helps organizations drill down into the most immediate issues that require attention. By viewing the data, the risk manager can save time and man-hours by addressing the most severe risks identified. This component displays vulnerability counts present on all vulnerability instances, exploitable vulnerabilities, remotely exploitable, low complexity, no authentication required vulnerabilities and those with the highest VPR score.
- Worst of the Worst - Top 10 Prioritized Actions - This table utilizes the remediation summary tool to focus on the top 10 prioritized actions to reduce risk immediately in the network. The data displayed takes into account the superdense of patches allowing for one action to remediate several identified vulnerabilities. The filters identify the solutions for the worst vulnerabilities and focuses on specific CVSS vectors to focus on the most essential actions.
- Worst of the Worst - Top 10 Must Remediate Vulnerabilities - This table utilizes the vulnerability summary tool to focus on the top 10 vulnerabilities that should be remediated first. The data displayed takes into account the VPR score, exploitability, and CVSS vectors. The filters identify the worst vulnerabilities and focuses on specific CVSS vectors to concentrate on the most essential actions.
- Worst of the Worst - 10 Most Vulnerable Assets - This table provides information on the Top 10 most vulnerable assets, providing the total number of vulnerabilities, score, IP address, DNS Name and OS CPE. The data displayed takes into account the VPR score, exploitability, and CVSS vectors. The filters identify the worst assets and focuses on specific CVSS vectors to concentrate on the most essential actions.
- Worst of the Worst - 90 Day Vulnerability Trend -This trend displays visually the worst of the worst vulnerabilities. Filters contain VPR 9-10. Trend lines could reflect new highs/lows over time, specifically the last 90 days. Note should be taken that as the VPR score and Predictive Prioritization changes over time, based on threat intelligence data, this area chart will also change.
- Worst of the Worst - OS/Application/No CPE Vulnerabilities - The data provided in this matrix allows the risk managers to view vulnerability data that applies to applications apart from operating systems. The filters use CPE strings to identity application or OS level vulnerabilities.
- Worst of the Worst - New Vulnerabilities Published Last 30 Days - Vulnerabilities continue to be released into the wild at a growing rate every year. This table displays vulnerabilities that have been published during the last 30 days. This component provides notification to organizations on these newly released vulnerabilities, allowing teams to identify emerging threats that may have previously been unknown.
- Worst of the Worst - By Asset - This table provides information on the most vulnerable assets group. Risk teams are presented with the total number of vulnerabilities and vulnerabilities by severity. The data displayed takes into account the VPR score, exploitability, and CVSS vectors under an Asset Summary. The filters identify the worst asset groups and focuses on specific CVSS vectors to focus on the most essential actions.
- Worst of the Worst - Certificate Concerns by Asset - This component focuses results around three primary SSL Certificate Plugins and help to track the certificates that are no longer valid or trusted. This is a key factor in determining that certificates need to be renewed prior to expiration dates to avoid denial of services for users.