Using the Service Location Protocol (SLP) to Find Exposed Management Interfaces

Exposed management interfaces are valuable entry points for attackers. CISA Binding Operational Directive 23-02 calls for getting them off the internet. Here’s a novel approach for finding some of these elusive devices using SLP.
The Cybersecurity and Infrastructure Security Agency (CISA) recently published Binding Operational Directive (BOD) 23-02 instructing U.S. federal agencies to get management interfaces off the internet in order to mitigate risk. CISA defines a networked management interface as a “dedicated device interface that is accessible over network protocols and is meant exclusively for authorized users to perform administrative activities on a device, a group of devices, or the network itself.”
While the CISA guidance is specific to U.S. federal government agencies, the issue is important to any organization. Servers and appliances often have management interfaces used for remote configuration and management of the device. These are typically connected to an out-of-band network segment, but are sometimes inadvertently connected to the Internet either physically or logically. Since these are used to manage servers, networking hardware and more, it’s important for any organization to ensure they are not exposed directly to the internet. They can be difficult to find for several reasons:
- Networked management interfaces are often proprietary per vendor and may look like just another service in hundreds or thousands of legitimate services offered by an organization.
- Networked management interfaces may not have any public vulnerabilities associated and therefore won’t be identified via a vulnerability management program.
While there are many ways to identify networked management interfaces that are exposed on the internet, this blog showcases a novel approach that may be useful for finding hard-to-identify devices.
Discovering SLP information
Service Location Protocol (SLP) provides a method to discover information about network services including their existence, location and configuration. Two agent types are used by SLP to catalog and advertise services: a service agent (SA) deals with one or more services while a directory agent (DA) handles services across multiple service agents. Most frequently, service agents advertise services running on the same host while directory agents deal with services across multiple hosts. The services cataloged by SLP include network services, printers, cameras, directory services, storage networks, virtualization infrastructure, web services, automotive systems and more. We can use SLP data obtained from service agents to hunt for services that most likely describe networked management interfaces.
The following plugins for Tenable Vulnerability Management (formerly Tenable.io), Tenable Security Center (formerly Tenable.sc) and Tenable Nessus can be used to send specific SLP requests and parse the results:
|
Plugin ID |
Name |
|
SLP Server Detection (UDP) |
|
|
SLP Server Detection (TCP) |
|
|
SLP Find Attributes |
The output from the first two SLP Server Detection plugins identifies whether or not the remote host is running the SLP service, whether it’s a directory agent or a service agent, and what services the SLP server knows about. The last plugin, SLP Find Attributes, issues an SLP attribute request command for every service discovered in the first two plugins. This causes the SLP server to list all the attributes it knows about that service, a possible treasure trove of information.
Attributes can be defined per service or even ad-hoc, so the attribute data retrieved does require some analysis. However, looking through SLP data for a scan can show hosts that are leaking information.
Example of plugin 23778 indicating SLP services
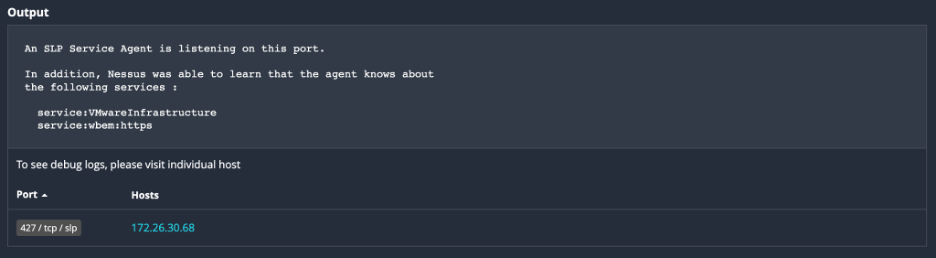
Image Source: Tenable, July 2023
Example of plugin 175142 indicating SLP service attributes
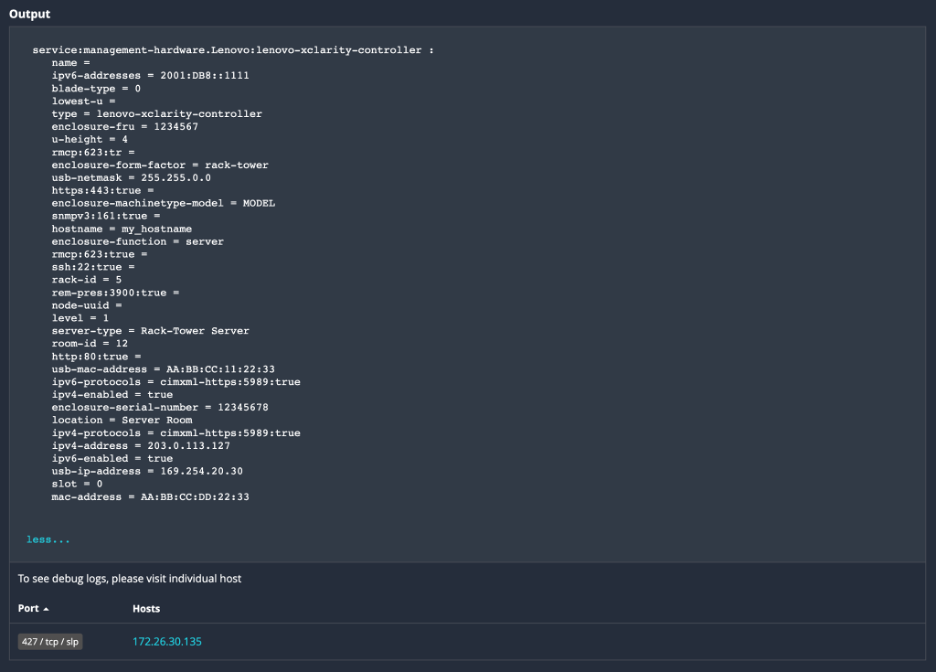
Image Source: Tenable, July 2023
Finding management interfaces
Out-of-band server management interfaces, such as integrated management module (IMM), integrated lights-out (iLo) and integrated Dell remote access controller (iDRAC), can be observed by SLP. It can also identify management interfaces for storage devices, printers and more. The following list of SLP services may include attribute information relating to networked management interfaces:
|
SLP Service Name |
What does it expose? |
|
service:VMwareInfrastructure |
VMWare ESX & ESXi |
|
service:cmm.smci |
Supermicro Update Manager (SUM) |
|
service:api:https |
Dell and HPE storage |
|
service:lenovo-smm |
Lenovo System Management Module |
|
service:management-hardware.Lenovo:lenovo-xclarity-controller |
Lenovo xclarity Controller |
|
service:x-mgmt.avago:lsa |
Intel/Avago RAID Management |
|
service:raid.001378:http |
Storage devices (QSAN, etc) |
|
service:printer |
Printers |
|
service:management-hardware.IBM:integrated-management-module2 service:management-hardware.IBM:integrated-management-module |
IBM Management Module |
Table Source: Tenable, July 2023
While there are more services worth exploring, these are some of the most common.
A quick scan of the internet for just service:management-hardware or service:management-software services reveals a few listening hosts, though there may be more:
|
Observed Hosts |
SLP Service Name |
|
10,611 |
service:VMwareInfrastructure |
|
61 |
service:management-hardware.IBM:integrated-management-module2 |
|
58 |
service:managemen t-hardware.Lenovo:lenovo-xclarity-controller |
|
3 |
service:management-software.IBM:platform-agent |
|
3 |
service:management-hardware.IBM:integrated-management-module |
|
1 |
service:management-software.IBM:hardware-management-console |
Table Source: Tenable, July 2023
For example, the screenshot below shows the web interface for one of the devices discovered using the above scan.
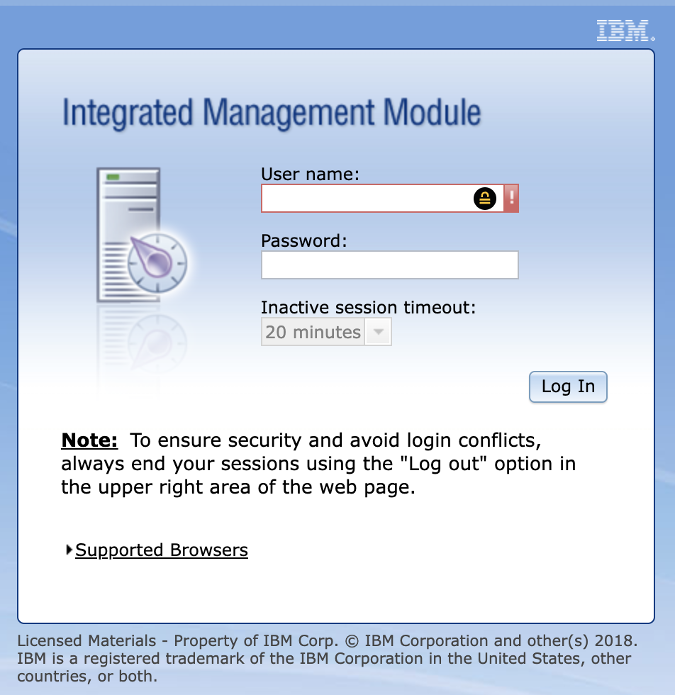
Image Source: Screenshot taken by Tenable of an IBM web interface discovered during an example scan, July 2023
Some of these exposed services may also indicate an internal and external IP address.
service:raid.001378:http
(vendor=Qsan Technology),(model=PerseusAPL),(product=XN3004T),(type=UNIFIED),(hostname=XXXXXX),(version=3.4.2),(builddate=202211290200),(dev=LAN1),(link=Up),(ip=192.168.X.X),(remoteip=XXX.XXX.XXX),(mac=00:13:78:XX:XX:XX),(serial=XXXXXXXXXX),(httpPort=13080),(httpsPort=13443),(webReady=Yes),(flags=0x3),(bpl=XXXX),(qlinkHost=),(qlinkPort=)We can see that a QSAN NAS device is hosting a management interface on the internal network and internet on ports 13080 and 13443, which correspond with documented management interfaces for these devices.
In Nessus, results will look like this:
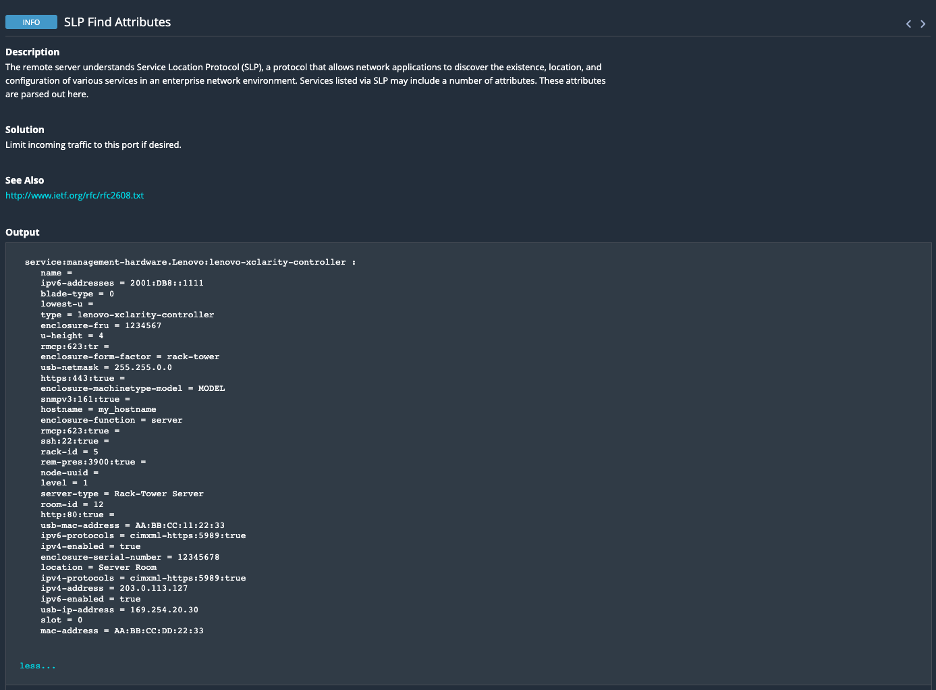
Image Source: Tenable, July 2023
Conclusion
Exposed management interfaces are extremely valuable for attackers seeking to find ways into an organization. While there are several ways to identify these exposed management interfaces, we strongly encourage customers to look through the output of the three SLP Nessus plugins on external scans. Wherever those plugins indicate services, especially the services detailed above, investigate the details and check that the listed IPs and ports aren’t exposed to the internet. Also check that the information exposed over SLP is expected for your organization because quite often it is not.
Many recent articles show the importance of keeping management interfaces secured:
- Firmware vulnerabilities in millions of computers could give hackers superuser status
- Some potential: How bad software updates could over-volt, brick remote servers
- Row erupts over who to blame after NordVPN says: One of our servers was hacked via remote management tool
- F5, Cisco admins: Stop what you're doing and check if you need to install these patches
- Researchers find high-severity command injection vuln in Fortinet's web app firewall
- QCT Servers Affected by ‘Pantsdown’ BMC Vulnerability
- NVIDIA Patches AMI BMC Vulnerabilities Impacting Several Major Vendors
Finding exposed management interfaces can be difficult but is an important part of modern attack surface management. CISA intends to scan U.S. federal government agencies and alert them to the presence of exposed management interfaces. Having additional methods to identify exposure will help all organizations understand their exposure and provide additional time to remediate for those in scope for the CISA BOD. Further, customers can utilize all aspects of vulnerability management including Nessus perimeter scans, utilizing audit files, and utilizing Tenable Attack Surface Management (formerly Tenable.asm).
Learn more
- Read the CISA BOD 23-02 here: https://www.cisa.gov/news-events/directives/binding-operational-directive-23-02
- Review the CISA BOD 23-02 Implementation Guidance here: https://www.cisa.gov/news-events/directives/binding-operational-directive-23-02-implementation-guidance
- Review the Tenable Security Center (formerly Tenable.sc) Out of Band Management Dashboard: https://www.tenable.com/sc-dashboards/out-of-band-management
Related Articles
- Research
- Attack Surface Management
- Exposure Management
- Vulnerability Management








