How to Protect Scanning Credentials: Overview

Running remote vulnerability scans of your network? This three-part blog series will equip you with tips on how to keep your scanning credentials safe.
Assessing systems remotely on a network has been a tried-and-true method of open-source and commercial vulnerability scanning since its inception over 20 years ago. External assessments like this are excellent for automatically testing visible network services and finding vulnerabilities or misconfigurations that may expose sensitive information.
A default scan is a remote, unauthenticated test. Unless you’re missing a patch to an exposed network service (e.g., EternalDarkness), this type of scanning won’t provide much detail on missing OS or third-party patches or compliance-related benchmarks (e.g., CIS Benchmarks or DISA STIGs) because they cannot look into the system being scanned and run the proper tests.
Actual results will vary, but it’s not uncommon to see a 10x increase in the number of vulnerabilities reported between an authenticated and unauthenticated scan (Tenable.io and Tenable.sc customers can use Predictive Prioritization and VPR to help manage this vulnerability overload). These vulnerabilities always existed; authenticated assessments provide visibility that an unauthenticated one cannot.
Thus, a question we often get is: “How do I ensure credentials used for vulnerability scanning are protected?” This is a great thought process for analysts to work through, and there are several things that organizations can do across the board to ensure credentials are secure.
5 ways to protect scanning credentials
- Use a unique account for vulnerability assessments.
There is no reason to share the account used for vulnerability assessments. Create a new one dedicated to this purpose, or have multiple accounts, depending on the complexity of your organization. Accounts should only exist on the systems they apply to (with applicable permissions). Tenable allows you to specify as many accounts as needed to run assessments.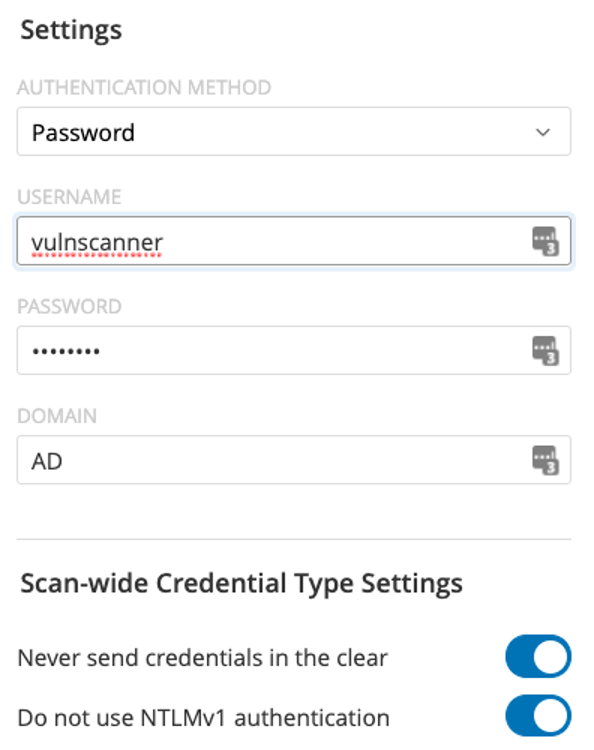
- Store credentials in encrypted data stores and/or with appropriate user access (i.e., use privileged access management).
Storing network passwords in a text file or spreadsheet is definitely a bad idea. Instead, use a system built and designed to store this data securely. Tenable integrates with a variety of solutions to enable customers to use these types of tools. - Only use secure protocols to authenticate to systems on your network.
There are lots of ways to authenticate to a system in today's networks. Some protocols are clear-text or have known vulnerabilities that make them trivial to compromise. Don’t use these protocols to authenticate to your systems. Though it can use plain-text protocols, the Nessus scanner defaults to only using secure protocols to authenticate to target systems. - Restrict when and how accounts are allowed to be used.
If you’re scanning your network every Sunday morning, then there should never be a reason your scanning account is used on a Tuesday from the intern’s laptop. Some platforms also allow accounts to be restricted to only use certain (e.g., secure) protocols. If you can restrict usage of your scanning account(s) to when they’re actually expected, how they authenticate to the targets, and from what systems, then definitely do so.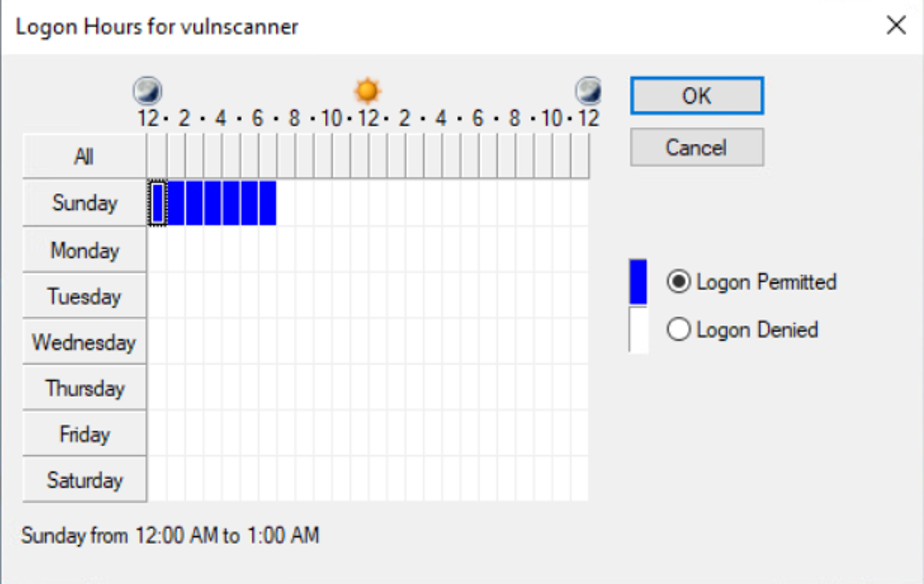
- Monitor accounts used for anomalies.
If you’re using a dedicated account for scanning or only scanning at certain times, then the usage of that account should be predictable, be it the source of the login attempts (Nessus) or the times of authentication attempts. Don’t overlook the verification component of control implementation.
3 things to avoid
- Do not reuse accounts between scanning and users or other IT operations.
There is no reason to reuse accounts for vulnerability assessments. Accounts should be single-use. - Do not use memorable or recycled passwords.
Because these passwords won’t ever be typed in manually by a human, they don’t need to be memorable or reused. They should be complex, long and unique.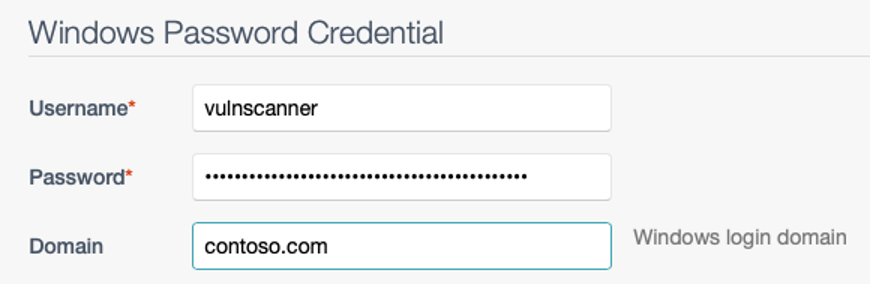
- Don’t change passwords too frequently.
Unless automated, changing scanning passwords too frequently can lead to scan errors and frustration. Where possible, only manually change passwords due to organizational policy or incident.
Next time, we’ll discuss Windows credentialed assessments and how you can secure them.
Note: There are alternatives to credentialed network scanning, such as agents and passive assessments.
Learn more
Read the online documentation:
Other blog posts in this series:
- 5 Ways to Protect Scanning Credentials for Windows Hosts
- 5 Ways to Protect Scanning Credentials for Linux, macOS and Unix Hosts
Explore related webinars:
- Automate Your Credentialed Vulnerability Assessments
- Overcoming the Challenges of Credentialed Scanning
Watch how-to videos:
Related Articles
- Nessus
- SecurityCenter
- Tenable.io
- Vulnerability Management
- Vulnerability Scanning







