Cybersecurity Snapshot: How To Boost the Cybersecurity of AI Systems While Minimizing Risks

Check out expert recommendations for deploying AI tools securely. Plus, the World Economic Forum ranks cyberattacks and AI misinformation among today’s top global risks. In addition, cyber insurance demand is forecast to grow robustly. And a warning about adversary-in-the-middle (AiTM) attacks and how to mitigate them. And much more!
Dive into six things that are top of mind for the week ending January 12.
1 - How to ensure AI helps, not hurts, cybersecurity
How can organizations use artificial intelligence (AI) in a way that’s safe and that benefits cybersecurity? That’s the question the non-profit thinktank Aspen Institute attempts to answer in its new report “Envisioning Cyber Futures with AI,” released this week.
Here’s a sampling of recommendations the report authors believe will help companies maximize the advantages of AI, while limiting its risks:
- Apply core cybersecurity principles to AI deployments, such as identity and access management controls, vulnerability management and asset management
- Make sure the AI team communicates and collaborates with other teams, including cybersecurity, legal, data science and executive leadership
- Proactively determine the decisions AI systems will be allowed to make
- Anticipate that AI-powered cyberattacks will be harder to detect, so sharpen your data logging, log review and log maintenance
- Be transparent about the outcomes your organization expects to reap from its AI use
- Include AI “rules of engagement” in your contracts
- Don’t get caught up in the AI frenzy and use the technology only where it’s warranted

Jen Easterly, Director of the U.S. Cybersecurity and Infrastructure Security Agency (CISA), said in a statement that the report will help support “secure by design” AI development and deployment.
“As nations and organizations embrace the transformative power of AI, it is important that we provide concrete recommendations to AI end users and cultivate a resilient foundation for the safe development and use of AI systems,” she added.
The paper is the work of the Aspen Institute's U.S. and Global Cybersecurity Groups, composed of cyber experts from major tech vendors; CISOs from multinational enterprises; professors from large universities; officials from government cyber agencies; and leaders from industry groups.
To get more details, check out:
- The announcement “Aspen Institute’s US and Global Cybersecurity Groups Unveil Guidelines for Secure and Responsible AI Deployment”
- The full report “Envisioning Cyber Futures with AI”
For more information about developing and deploying AI systems securely:
- “Want to Deploy AI Securely? New Industry Group Will Compile AI Safety Best Practices” (Tenable)
- “Evaluate the risks and benefits of AI in cybersecurity” (TechTarget)
- “Assessing the pros and cons of AI for cybersecurity” (Security Magazine)
- “8 Questions About Using AI Responsibly, Answered” (Harvard Business Review)
- “Guidelines for secure AI system development” (U.K. National Cyber Security Centre)
VIDEO
Ultimate Guide to AI for Businesses (TechTarget)
2 - WEF: Cyberattacks, AI misinformation among top global risks
False information generated using artificial intelligence (AI) ranks among the world’s top five risks today, and will become the most severe risk in two years. Meanwhile, the risk of cyberattacks ranked fifth among today’s top risks, and will be the fourth most severe risk two years from now.
That’s according to the World Economic Forum’s “Global Risks Report 2024,” published this week. Extreme weather ranked first, while societal / political polarization and cost-of-living challenges rounded out the top five global risks for 2024.
Current Risk Landscape
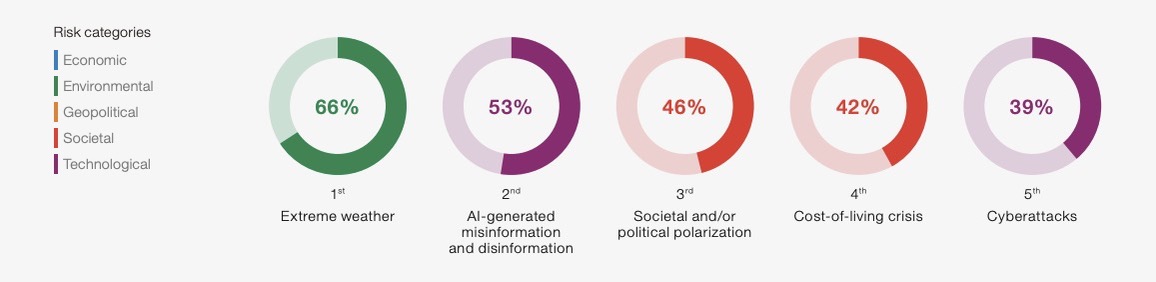
(Source: World Economic Forum’s “Global Risks Report 2024” report, January 2024)
Cracking the top 10 global risks ranking for the first time in the WEF report’s 19-year history, AI-generated misinformation and disinformation could lead to:
- Election disruptions
- Civil unrest and societal polarization tied to distrust of information
- Government repression of civil rights
“Artificial intelligence breakthroughs will radically disrupt the risk outlook for organizations with many struggling to react to threats arising from misinformation, disintermediation and strategic miscalculation,” Carolina Klint, Europe Chief Commercial Officer at Marsh McLennan said in a WEF statement.
Meanwhile, cyberattacks, which include cyberwarfare, cyberespionage and cybercrime, will continue to escalate, as malicious actors get access to new, easy-to-use tools and technologies to boost and further spread their criminal activities against individuals, businesses and governments.
“Advances in technology will break down barriers to entry – borders, languages, skill sets – opening alternate revenue streams, particularly in the cyber domain, and allowing transnational criminal networks to spread,” the report reads.
Global Risks Ranked by Severity over the Short Term (2 years)
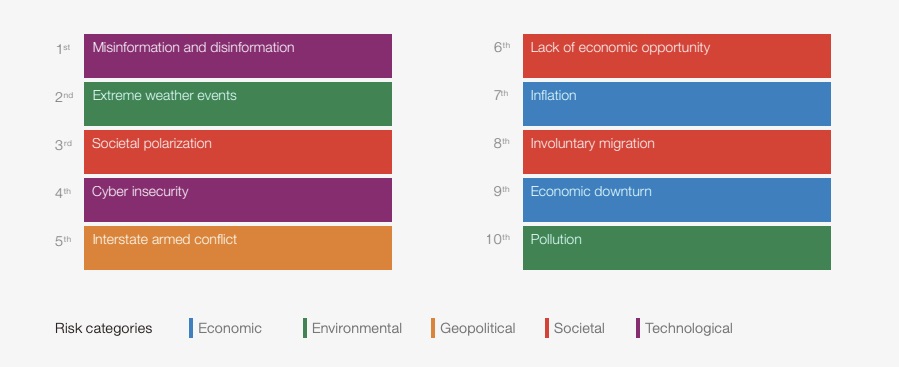
(Source: World Economic Forum’s “Global Risks Report 2024” report, January 2024)
So what can be done? Here are some WEF recommendations for reducing risks related to cyberattacks and AI misuse:
- Governments should promote public awareness and education on the impact of AI-enabled misinformation, and raise their citizens’ level of AI literacy
- Governments and businesses should partner to invest in research and development projects, whose advances can help tackle cybercrime and adverse outcomes of AI
- Cross-border coordination in the form of global treaties and agreements can help make a dent in cybercriminal activities and malicious uses of AI
The annual report is based primarily on a risk-perception survey of about 1,500 experts, and on an opinion survey of about 11,000 business leaders worldwide.
To get more details, check out:
- The WEF’s announcement “Global Risks 2024: Disinformation Tops Global Risks 2024 as Environmental Threats Intensify”
- The full “Global Risks Report 2024”
- These videos:
3 - Strong growth projected for cyber insurance
The growing number and frequency of cyberattacks. Stricter and more complex data protection and privacy regulations. Mounting financial losses stemming from cyber breaches.
Those are some key drivers fueling demand for cybersecurity insurance, a market expected to grow at a 22.3% compound annual rate and reach almost $91 billion globally by 2033.
That’s according to the new report “Global Cyber Insurance Market” from market research and analysis firm Market.us, which estimates the market hit $12.1 billion in 2023.
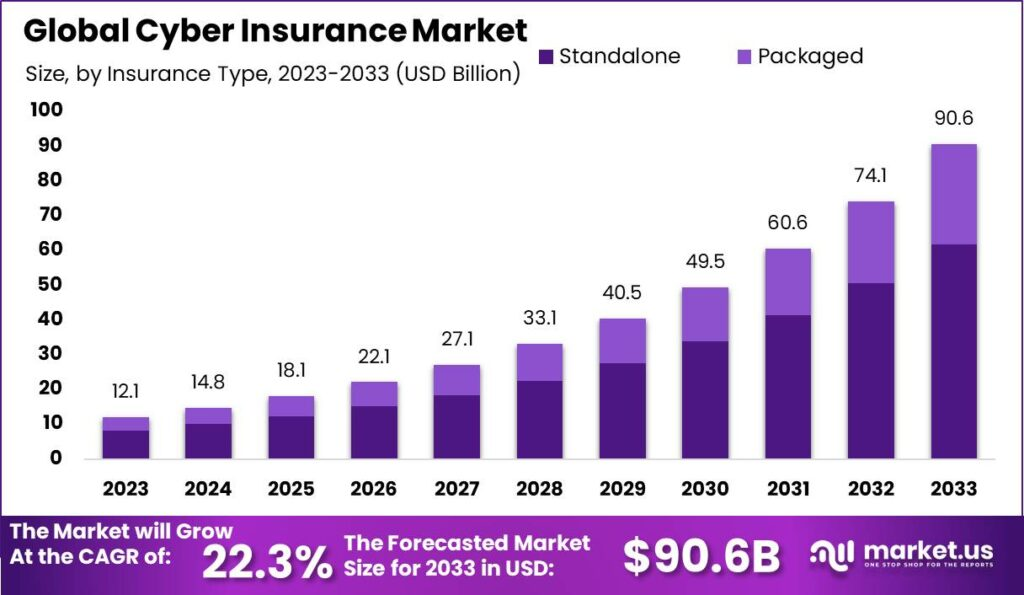
Despite the expected growth in demand, the cyber insurance market also faces headwinds, including a lack of standardization, limited understanding of risks and increasingly sophisticated cyberattacks, according to the report.
Other interesting findings include:
- Most cyber insurance coverage comes in the form of standalone policies (68.2%), while the remaining is bundled in with other types of insurance
- Coverage for third-party claims, such as from clients affected by an insured company’s data breach, accounts for 62.1% of the market
- Large enterprises account for 72.4% of the cyber insurance market
- Among industry verticals, the banking and financial services sector ranks first with a 28.3% share
For more information about cyber insurance trends:
- “5 Cyber Insurance Trends To Watch Right Now” (CRN)
- “How To Obtain the Right Cybersecurity Insurance for Your Business” (Tenable)
- “War or Cost of Doing Business? Cyber Insurers Hashing Out Exclusions” (Dark Reading)
- “New SEC Rules Add Challenges in Uncertain Cyber Insurance Market” (Bloomberg)
- “4 tips to find cyber insurance coverage in 2024” (TechTarget)
4 - UK cyber agency tailors cloud security tips for SMBs
Cloud security recommendations for large enterprises may be impractical for smaller organizations. Thus, the U.K. National Cyber Security Centre (NCSC) this week published new cloud security guidance crafted specifically for small and medium size businesses (SMBs).
The “Using online services safely” guide unpacks nine principles to help SMBs protect their cloud services. Here’s a sampling of the NCSC’s best practices:
- Choose cloud services that have been independently deemed secure, and opt for service versions that offer sufficient security features
- Ensure that the critical data you’re storing in a cloud service has been exported to another cloud or on-prem location and backed up
- Assign each employee an account to access the cloud service, as opposed to setting up one account that’s used by multiple staffers
- Secure cloud accounts using multifactor authentication (MFA) and require that users create unique, complex passwords
- Be particularly diligent about protecting admin accounts, since they control more capabilities and data than regular accounts
For more information about cybersecurity guidance for SMBs:
- “Cybersecurity for Small Businesses” (U.S. Federal Communications Commission)
- “The GCA Cybersecurity Toolkit for Small Business” (Global Cyber Alliance)
- “Cyber Guidance for Small Businesses” (CISA)
- “Strengthen your cybersecurity” (U.S. Small Business Administration)
- “Cyberattacks and Your Small Business: A Primer for Cybersecurity” (Business News Daily)
VIDEOS
Protecting your small business: Phishing (NIST)
Protecting your small business: Multifactor authentication (NIST)
Protecting your small business: Ransomware (NIST)
5 - CIS alerts U.S. local governments about AiTM phishing attacks
Local governments in the U.S. must be on guard against adversary-in-the-middle (AiTM) attacks, because launching them is becoming easier thanks to growing availability of phishing-as-a-service (PhaaS) open source tools.
So said the Center for Internet Security’s (CIS) Cyber Threat Intelligence (CTI) team at the Multi-State Information Sharing and Analysis Center (MS-ISAC) this week, in an advisory aimed specifically at U.S. state, local, tribal and territorial governments.
“In the past, effective AiTM phishing attempts required cyber threat actors (CTAs) to leverage strong technical capabilities. CTAs crafted a phishing email, built a convincing fake landing page, and set up the reverse proxy to capture the credentials,” reads a CIS blog.
“However, the popularity of Phishing as a Service (PhaaS) cybercrime options enables threat actors to purchase the necessary components out of the box. This has lowered the barrier of entry for CTAs with limited technical proficiencies,” the blog adds.
AiTM Attack Lifecycle
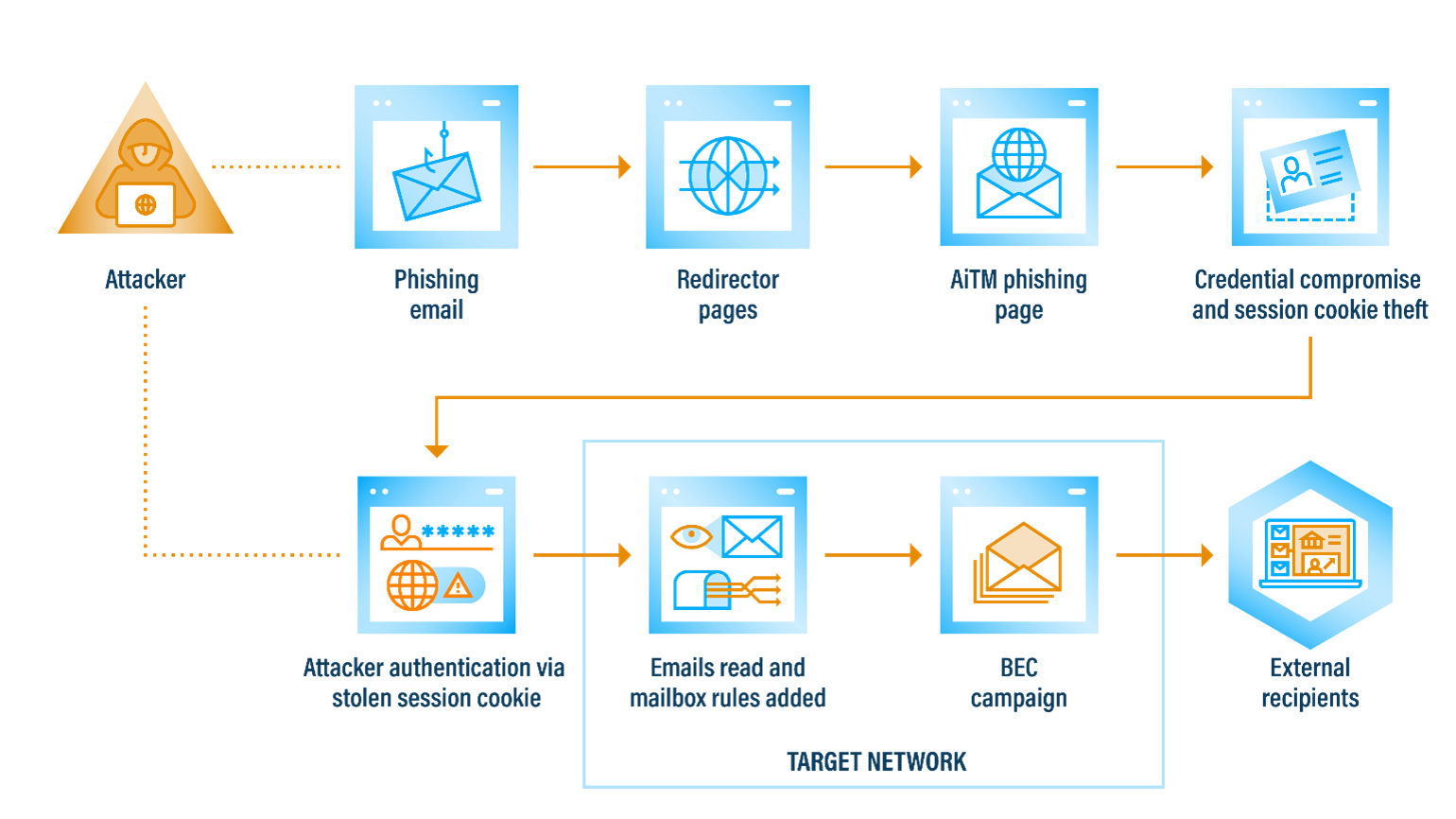
(Source: Center for Internet Security, January 2024)
To mitigate AiTM attacks, CIS recommendations include:
- Set conditional access policies within users’ MFA settings
- Prohibit self-signed certificates by creating group policies
- Perform continuous monitoring of suspicious activity, including sign-in attempts and MFA setting changes
- Mark emails from external sources
To get more details, read the blog “CTAs Using Adversary in the Middle (AiTM) Phishing Attacks.”
For more information about AiTM attacks:
- “What is an adversary-in-the-middle attack?” (MITRE)
- “Microsoft Warns of Adversary-in-the-Middle Uptick on Phishing Platforms” (Infosecurity)
- “Massive adversary-in-the-middle phishing campaign bypasses MFA and mimics Microsoft Office” (TechRepublic)
- “What is a man-in-the-middle (MiTM) attack?” (TechTarget)
6 - CIS updates Benchmarks for Amazon Linux 2, Oracle Database and others
CIS has announced the updates it made to its CIS Benchmarks in December, which include new secure configuration recommendations for AWS’ Amazon Linux 2 operating system (OS), Cisco’s NX-OS network OS and Oracle Database 19c.

Here’s the full list of updated CIS Benchmarks for December:
- CIS Amazon Linux 2 Benchmark v3.0.0
- CIS CentOS Linux 7 Benchmark v4.0.0 – final update
- CIS Cisco NX-OS Benchmark v1.1.0
- CIS Microsoft Windows Server 2019 STIG Benchmark v2.0.0
- CIS Oracle Database 19c Benchmark v1.2.0
- CIS Oracle Linux 7 Benchmark v4.0.0 – final update
- CIS Oracle Solaris 11.4 Benchmark v1.1.0 – final update
- CIS Red Hat Enterprise Linux 7 Benchmark v4.0.0 – final update
In addition, CIS also released these new Benchmarks:
- CIS Microsoft Windows Server 2019 Stand-alone Benchmark v1.0.0
- CIS Cisco Firepower Threat Defense Benchmark v1.0.0
- CIS Microsoft Windows Server 2022 STIG Benchmark v1.0.0
To get more details, read the CIS blog “CIS Benchmarks January 2024 Update.” For more information about the CIS Benchmarks list, check out its home page, as well as:
- “How to use CIS benchmarks to improve public cloud security” (TechTarget)
- “How to Unlock the Security Benefits of the CIS Benchmarks” (Tenable)
- “CIS Benchmarks Communities: Where configurations meet consensus” (HelpNet Security)
- “CIS Benchmarks: DevOps Guide to Hardening the Cloud” (DevOps)
CIS Benchmarks
Related Articles
- Cloud
- Exposure Management
- Risk-based Vulnerability Management
- Vulnerability Management
- Cloud
- Cybersecurity Snapshot
- Exposure Management
- Federal
- Government
- Vulnerability Management





