by Cesar Navas
December 19, 2019
Analyzing the perimeter of the network begins with first determining where the borders are logically located. The borders are not always the Edge or a firewall, but are now extended to remote workers, cloud services, and co-located data centers. This dashboard helps track systems that communicate with external devices, and track vulnerabilities related to well-known ports.
The CIS ControlsTM are a prioritized set of actions that collectively form a defense-in-depth set of best practices that mitigate the most common attacks against systems and networks. These controls were developed by IT professionals using operational experiences and generally accepted best practices. This dashboard will focus on Control 9 (Limitation and Control of Network Ports, Protocols, and Services) & Control 12 (Boundary Defense).
Historically CIS has referred the first six CIS controls as cyber hygiene to focus an organization’s cybersecurity activities. The designation of cyber hygiene brought up the fact that these practices may be difficult for organizations with resource and/or expertise limitations. To address any resource or expertise limitation, CIS now recommends following Implementation Groups (IG) to help prioritize CIS control utilization. There are three IG’s, which describe organization by size. The IG specifies a subset of the controls that have been assessed to have a similar risk profile and resources to implement. The IG’s are also meant to be prioritized in IG order regardless of the IG organization size; for example, organizations should implement Sub-Controls in IG1, followed by IG2 and then IG3. The IG’s are described as organizations with limited resources and cybersecurity expertise (IG1); Organizations with moderate resources (IG2); Organizations with significant resources (IG3).
CIS Control 9 requires organizations to manage (track/control/correct) the ongoing operational use of ports, protocols, and services on networked devices in order to minimize windows of vulnerability available to the attacker. One sub control applies to all IG’s, while the others only apply to IG 2 and IG 3. Sub Control 9.4 requires organizations to apply host-based firewalls, and Tenable.sc can check for firewall configurations in several ways. This dashboard focuses on the tracking of active ports, services and protocols. The asset inventory aspects of sub control 9.1, and automated port scanning in 9.3 is where Tenable.sc supports the greater objective referenced in this control.
Tenable.sc is able to routinely scan the network for open ports and services. Nessus scanners are capable of scanning internal and external assets on the network. Tenable.sc can also use passive detection to find systems that are communicating with the internal network from external or untrusted devices. This feature helps support sub control 12.2 (Scan for Unauthorized Connections across Trusted Network Boundaries). By using the active and passive detection methods, the risk management teams can better understand the risk to the organization and provide the necessary guidance to reduce risk.
The dashboard and its components are available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, assurance report cards and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Executive.
The dashboard requirements are:
- Tenable.sc 5.12.0
- Nessus 8.8.0
Tenable.sc Continuous View (CV) is the market-defining On-Prem Cyber Exposure Platform. Tenable.sc CV provide the ability to Analyze assets protocols in use, their open ports, and related services. By using active and passive detections Tenable.sc provides customers with a full and complete Cyber Exposure platform for completing an effective Cyber Hygiene program prescribed by CIS Controls framework.
This dashboard contains the following components:
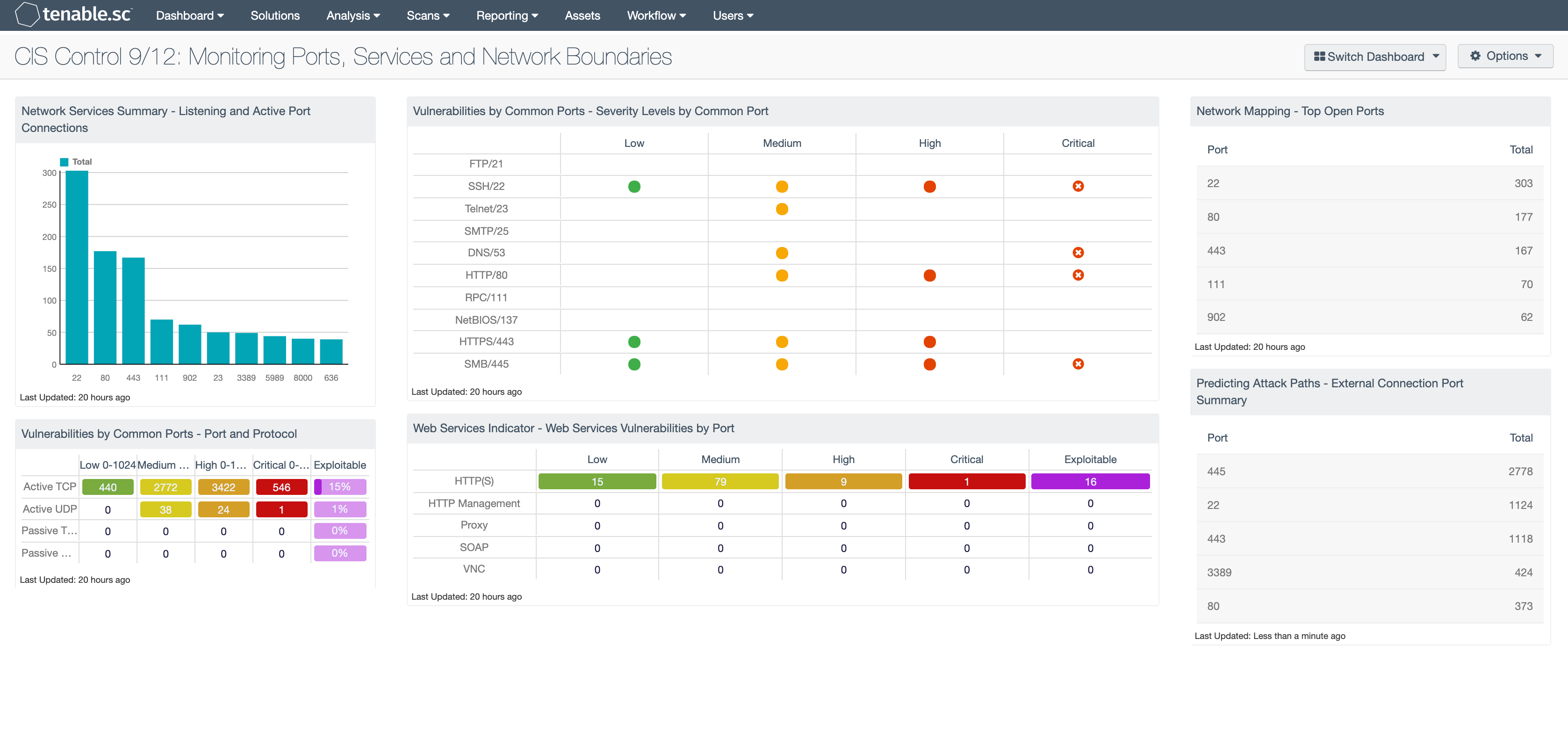
Network Services Summary - Listening and Active Port Connections: This bar chart presents the top 10 ports detected on hosts that are listening or have active port connections. Nessus provides several plugins that leverage the “Netstat” command to determine all listening and enabled connections on hosts. This component can be modified to include specific port connections per organizational requirements. Analysts can browse the component data to obtain additional information on hosts, services, and port activity.
Vulnerabilities by Common Ports - Port and Protocol: This matrix component provides a count of vulnerabilities by severity level, TCP port, and vulnerability type. The first two rows use active detection, while the bottom two use passive detection. For each detection method, there is a row for TCP and UDP. Port ranges from 0-1024, along with severity levels of low, medium, high, and critical, are used for each column. The last column provides a percentage of exploitable vulnerabilities. The raw results are displayed based on the severity level. The colors used are green (low), yellow (medium), orange (high), and red (critical). The last column in purple shows exploitability but makes no reference to severity level.
Vulnerabilities by Common Ports - Severity Levels by Common Port: This component effectively uses color and empty space to convey information about vulnerabilities and risk severity. Each column is a severity level of low, medium, high, or critical. Each row is a common popular port chosen at random. Using this matrix as a template, a security administrator can modify the matrix to use assets, IP addresses, plugin families, repositories, and more. The icon colors can communicate risk: green for low severity, yellow for medium, and red for high severity. For the critical severities, the red icon with white 'X' is used. When no match is found, the default setting is an empty display text field.
Web Services Indicator - Web Services Vulnerabilities by Port: This component checks for vulnerabilities for web services associated with common ports of the web services. Vulnerabilities for each web service are broken down by low, medium, high and critical severities. There is an additional column that shows the number of vulnerabilities that have public exploits available by web service. These vulnerabilities can be exploited by publically available tools and should be remediated as soon as possible.
Network Mapping - Top Open Ports: This table presents the top ports that were detected to be open by various active scanning techniques. The table is sorted so that the ports with the highest number of detections are at the top. This table displays ports that are detected to be open, not necessarily ports that are being actively used. To reduce the network attack surface, open ports that are not being used should be disabled. The data in this table does not count against the SecurityCenter licensing.
Predicting Attack Paths - External Connection Port Summary: This component uses information from plugin ID 14, “Accepts external connections”, and the Port Summary tool to present a table that is sorted by the most commonly observed active ports. The port column displays the TCP port, and the count column presents the number of systems detected. This allows the analyst to determine which ports are open externally.