How to Use Tenable.io WAS to Find and Fix Sensitive Information Exposure in Microsoft Power Apps

Researchers identified a configuration issue in Microsoft Power Apps portals that exposed millions of records for nearly 50 organizations. Learn how you can use Tenable.io Web App Scanning to identify this configuration issue and prevent the exposure of sensitive information.
Thanks to Satnam Narang from the Security Response Team for his contributions to this blog post.
Background
On August 23, UpGuard Research published a blog post detailing its discovery of the exposure of 38 million records across 47 entities via Microsoft Power Apps portals. Power Apps portals, as Microsoft describes them, allows both internal and external individuals to securely access Microsoft Dataverse data using portals.
According to UpGuard, the Power Apps portals are configured for public access by default, which means anonymous users could access this data. In their research, Upguard found the exposure of personally identifiable information (PII), including COVID-19 related contact tracing and vaccination appointment details, social security numbers, employee IDs, names and addresses and a variety of other sensitive information.
UpGuard disclosed its findings to Microsoft in June. Microsoft responded that the behavior is “considered to be by design” and UpGuard’s case was closed. However, as recent industry data shows, misconfigurations in cloud environments can increase an organization's risk of being breached.
Two-thirds of cloud breaches were due to misconfigurations
IBM’s 2021 X-Force Cloud Security Threat Landscape Report, which analyzed data sets from Q2 2020 through Q2 2021, found that two-thirds of cloud environment breaches could have been prevented if misconfigurations and policies were properly reviewed and addressed. IBM’s findings were centered around improperly configured APIs and virtual machines, but the overarching theme of misconfigurations is also applicable to Power Apps. However, the problem with the Power Apps exposure is that organizations likely did not realize they were exposing this information when UpGuard identified the exposure.
Analysis
As a low-code platform — an environment that supports development via a graphical user interface instead of hand-coding — Microsoft Power Apps allow users to build and publish web pages rendering data from multiple sources using connectors. Among the different application types offered by the platform, Power Apps portals provide a web view which can be accessed by authenticated or anonymous users. By leveraging the concept of lists, a Power Apps user is able to quickly render a set of records from the data source without the need to write code.
The problem with default table permissions in Power Apps
Power Apps portals rely on web roles and table permissions to define the privileges allowed to the different users on a given list, whether they are authenticated or not. By default, table permissions are not applied to lists and need to be explicitly enabled with an option in the list properties:
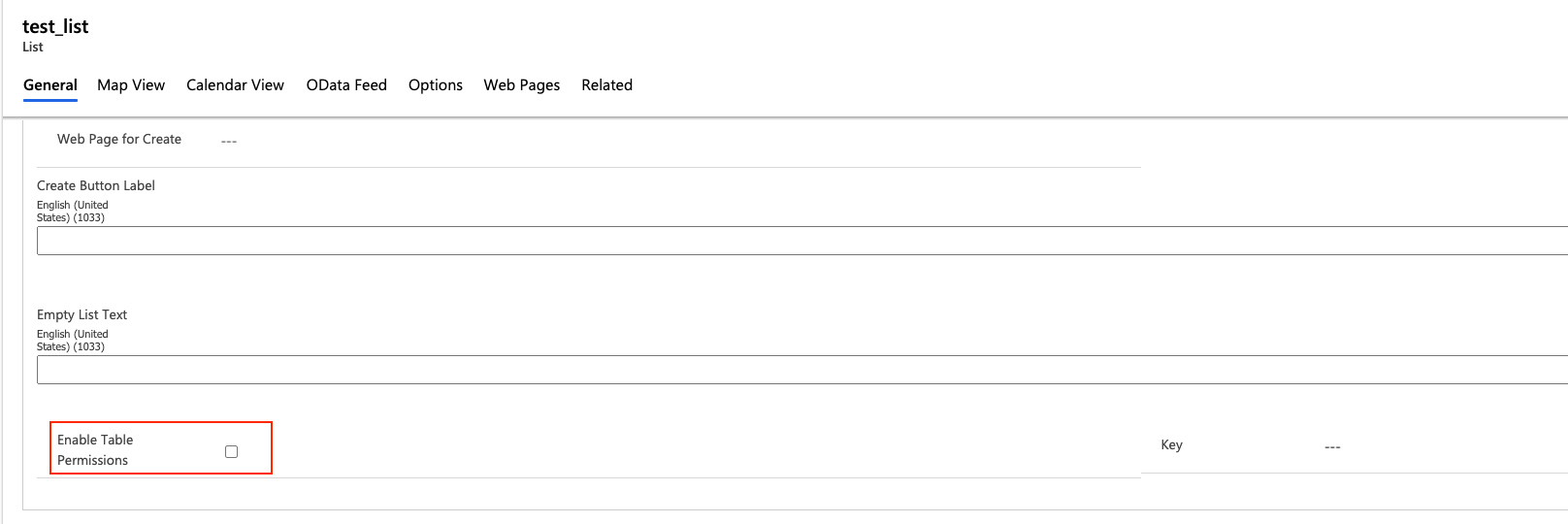
Source: Tenable Research, 2021
Usually, lists are included in web pages which have their own permissions settings, preventing the pages from being accessed by unauthorized or anonymous users.
Exposing sensitive information through OData feeds
A feature of Power Apps portals lists allows users to publish the underlying data feed as a RESTful web service through the OData protocol:
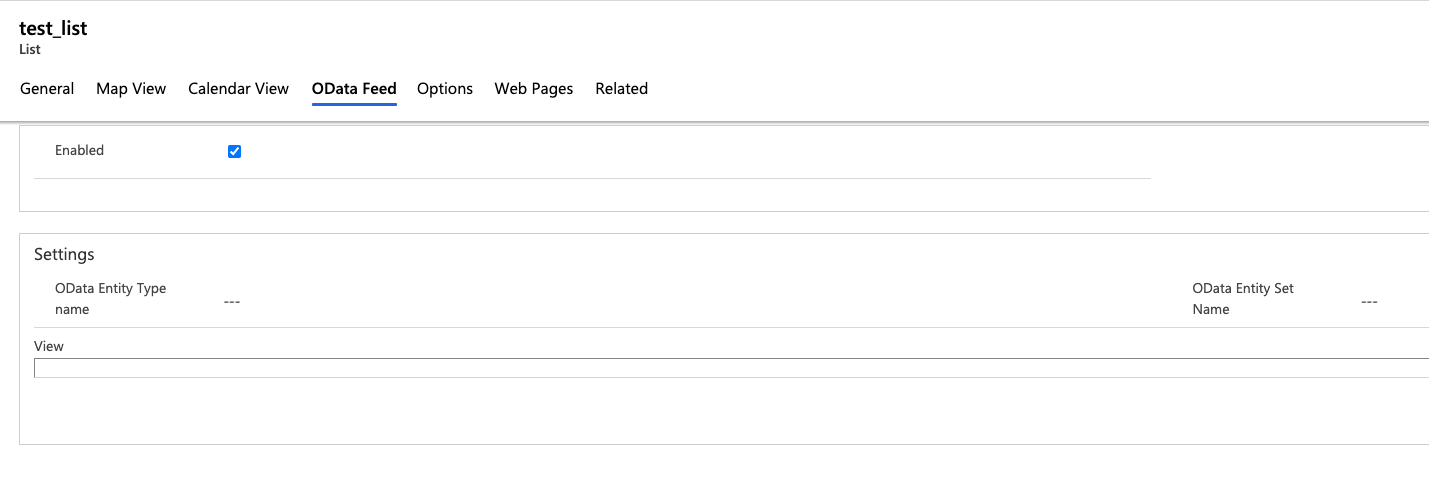
Source: Tenable Research, 2021
OData feeds define a specific endpoint on the target application, which exposes OData metadata and the list of feeds available:
Example endpoint: https://myportal.powerappsportals.com/_odata/
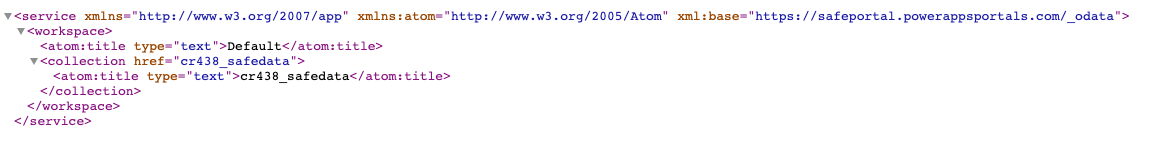
Source: Tenable Research, 2021
With the previous default configuration, table permissions were not enforced on the various data collections returned in the OData feed, leading to the data being exposed to any user with a query targeting specific collections like: Example endpoint: https://myportal.powerappsportals.com/_odata/collection
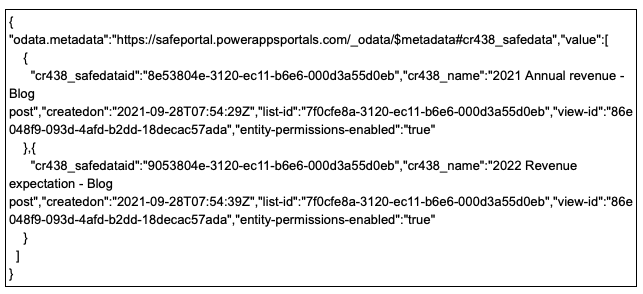
Source: Tenable Research, 2021
Solution
The mitigation of this configuration issue requires enforcing table permissions, especially when the OData feed is enabled.
Power Apps portals management can be achieved by using Power Apps portals Studio or with the Power Apps portal management application.
With Power Apps portals Studio, table permissions are enabled by default when adding a new entity to a page:
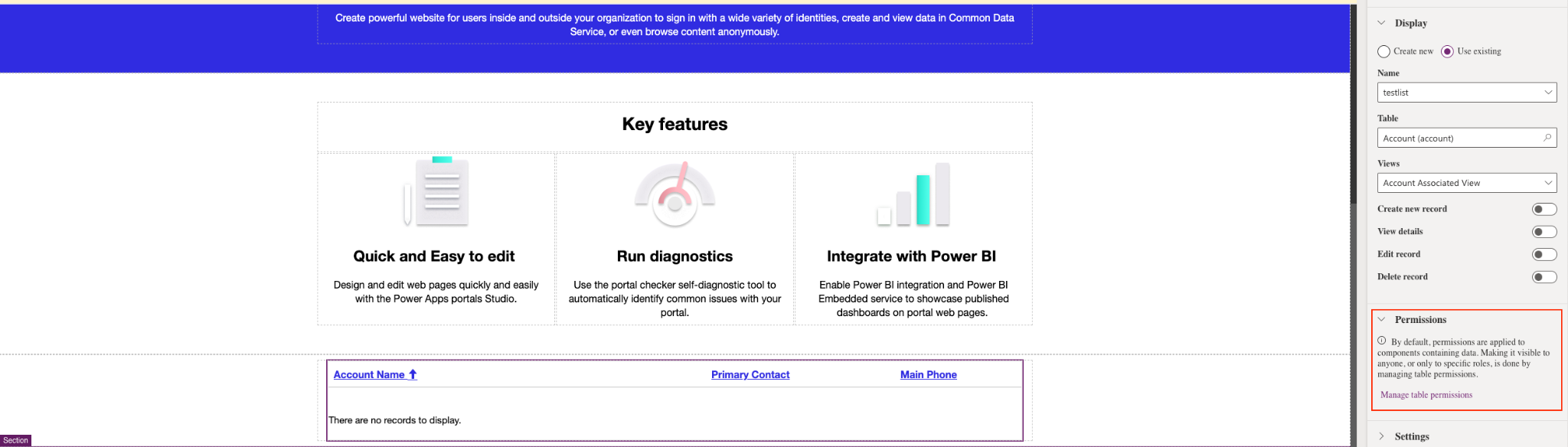
Source: Tenable Research, 2021
Browsing a live website with this option enabled and without any explicit permission will display an error:
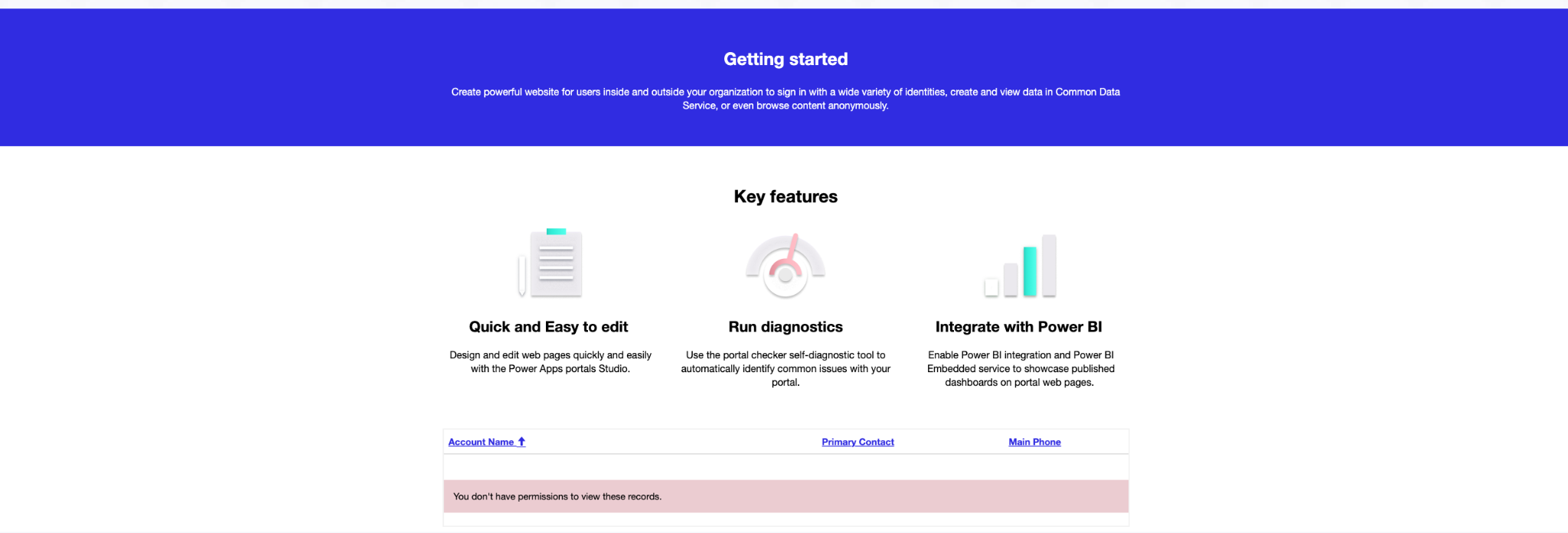
Source: Tenable Research, 2021
With Power Apps portal management, applications previously required users to enable the table permissions. Now, the option is set by default when creating an entity:
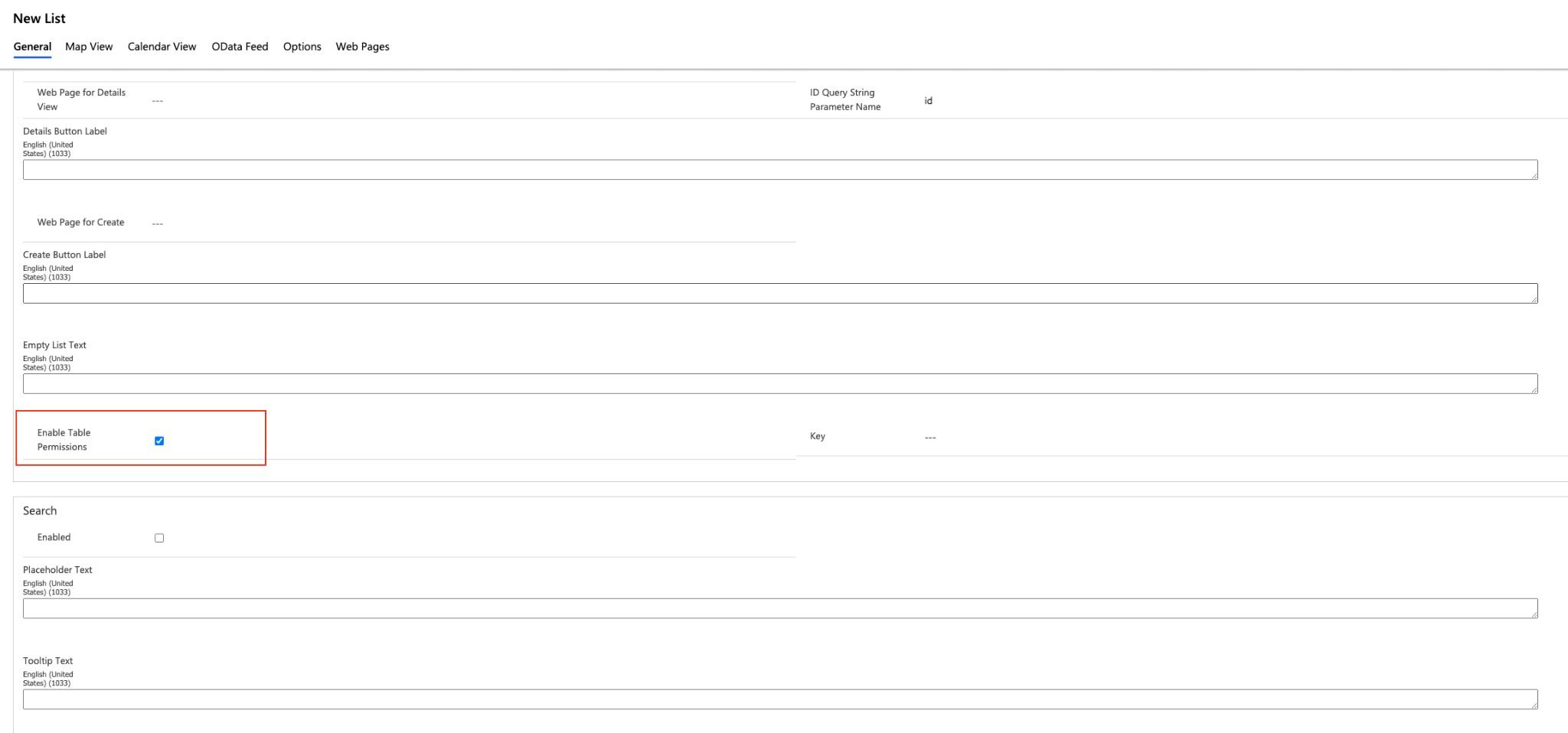
Source: Tenable Research, 2021
When trying to disable the table permissions, a warning is now displayed at the top of the Power Apps management console:
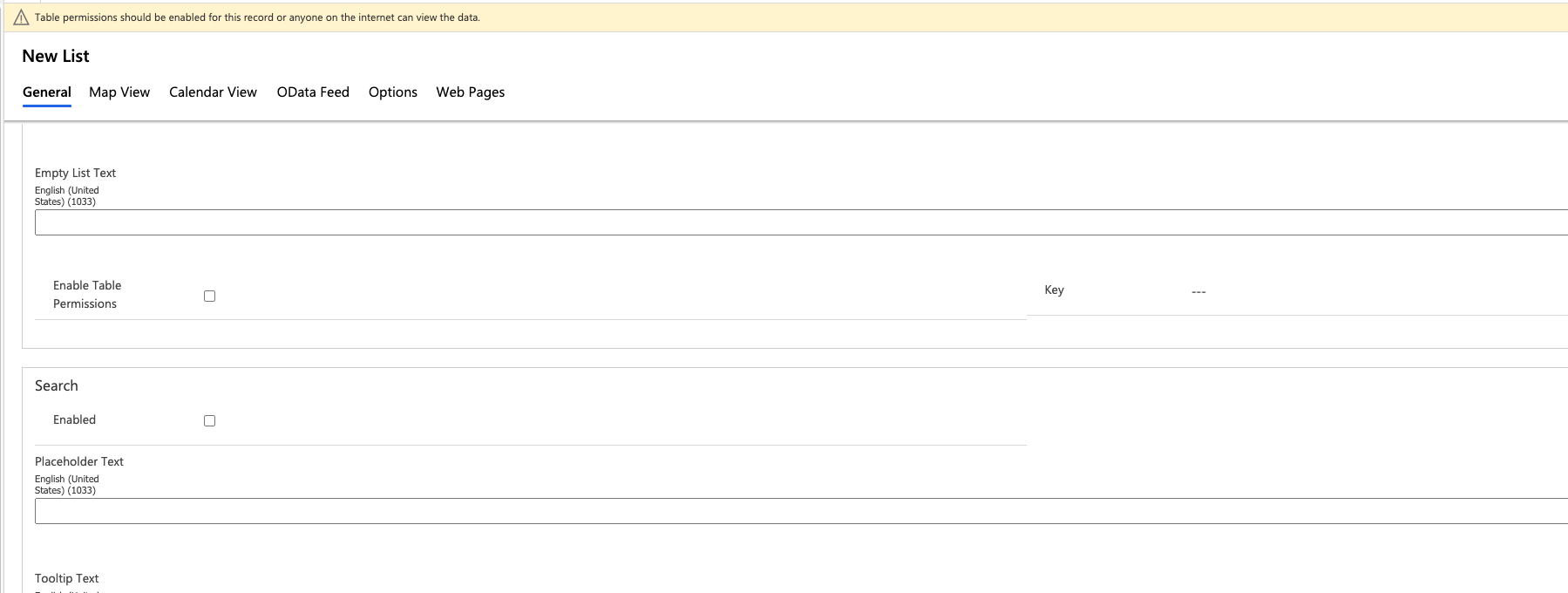
Source: Tenable Research, 2021
On July 15, Microsoft added release notes that include a configuration check for both existing and new portals to detect when the “Enable Table Permissions” is disabled when OData feeds are enabled:
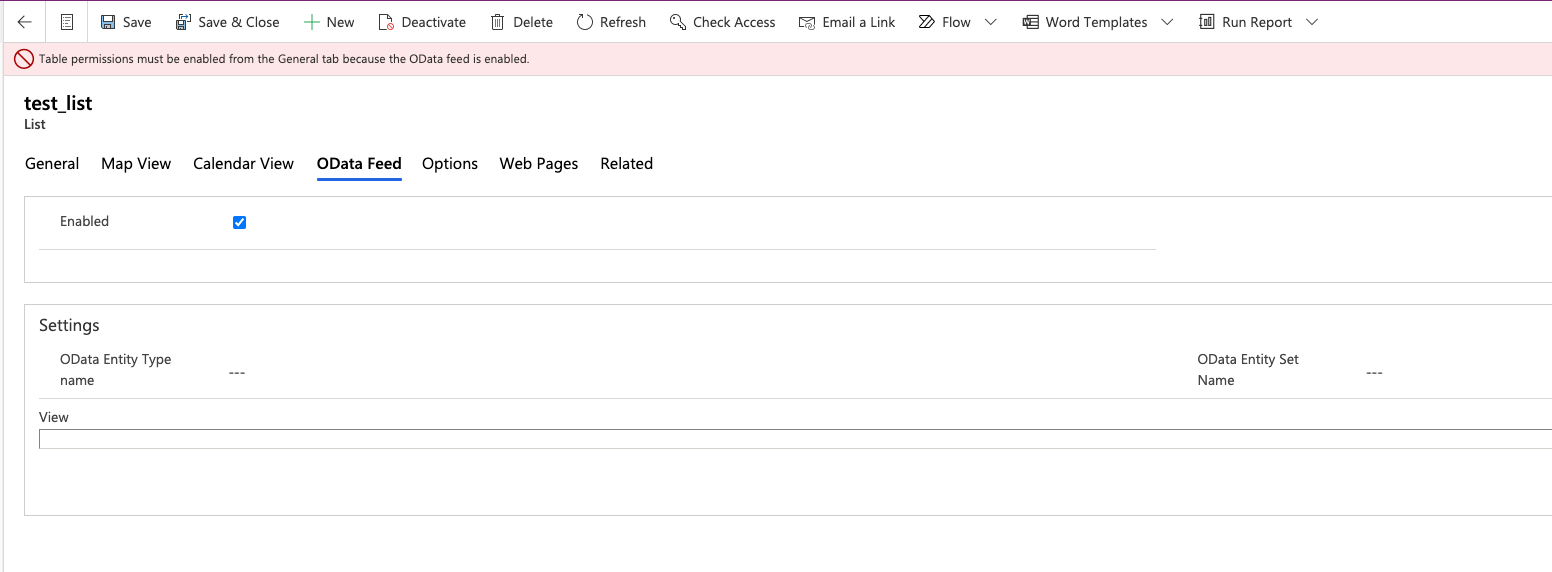
Source: Tenable Research, 2021
Finally, Microsoft added a warning message in the Power Apps portals Studio when one or more entities exists without table permissions. This alert warns users that the permissions will be enforced automatically starting in April 2022:
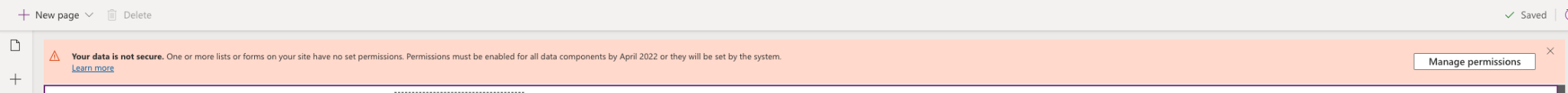
Source: Tenable Research, 2021
Note that enabling table permissions does not prevent Power Apps administrators from misconfiguring a table if, for example, they set anonymous access to lists containing sensitive data.
Identifying affected systems
Power Apps portals are software-as-a-service (SaaS) web applications hosted in the Microsoft Cloud platform. Tenable.io Web App Scanning offers two plugins to help customers identify applications built on the Power Apps platform and determine whether they are potentially exposing data.
The Power Apps Application Detected plugin is designed to verify if an application hosted on a custom DNS name is a Power Apps portal:
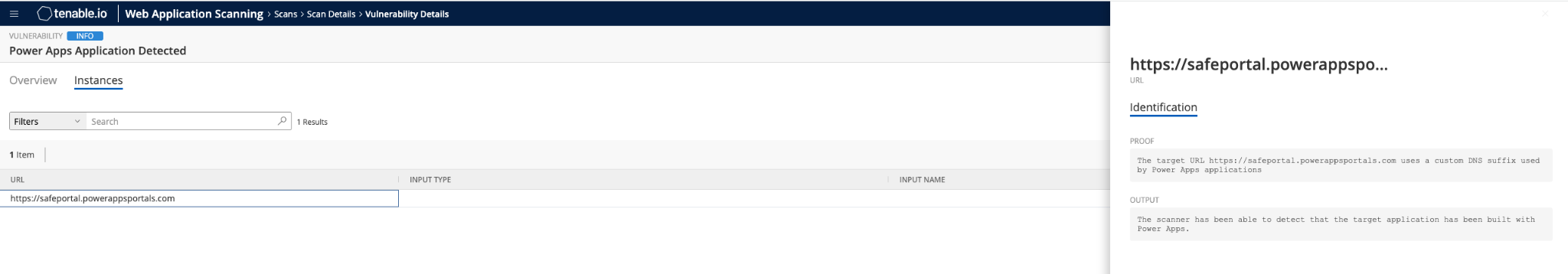
Source: Tenable Research, 2021
Once a Power Apps portal is detected, customers can use the Power Apps OData Feeds Detected plugin. This plugin performs a check on the OData feeds to identify collections that can be publicly accessed and their associated URLs. Web App Scanning users can then browse the list of collections to verify if any sensitive or unexpected data has been exposed.
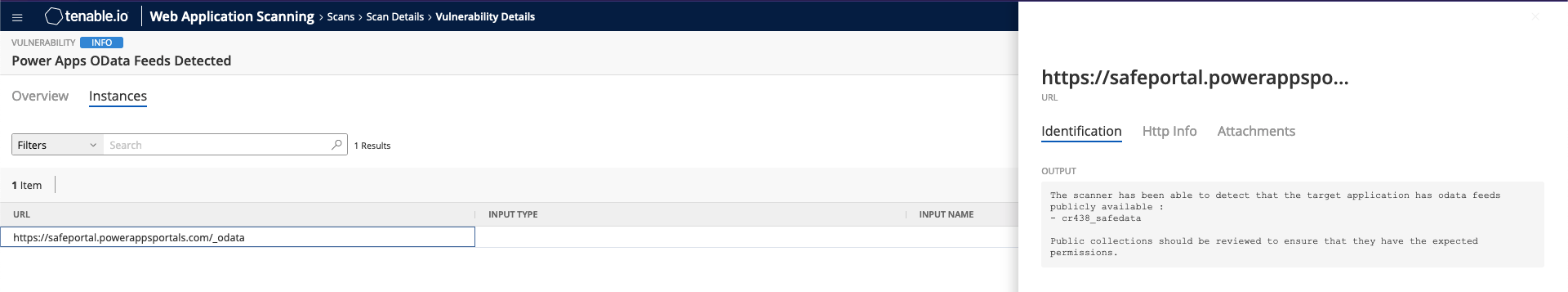
Source: Tenable Research, 2021
Note that Microsoft also provides the portal checker tool, which can be used in addition to Web App Scanning to allow administrators to run a configuration check on their portals and identify lists that allow for anonymous access:
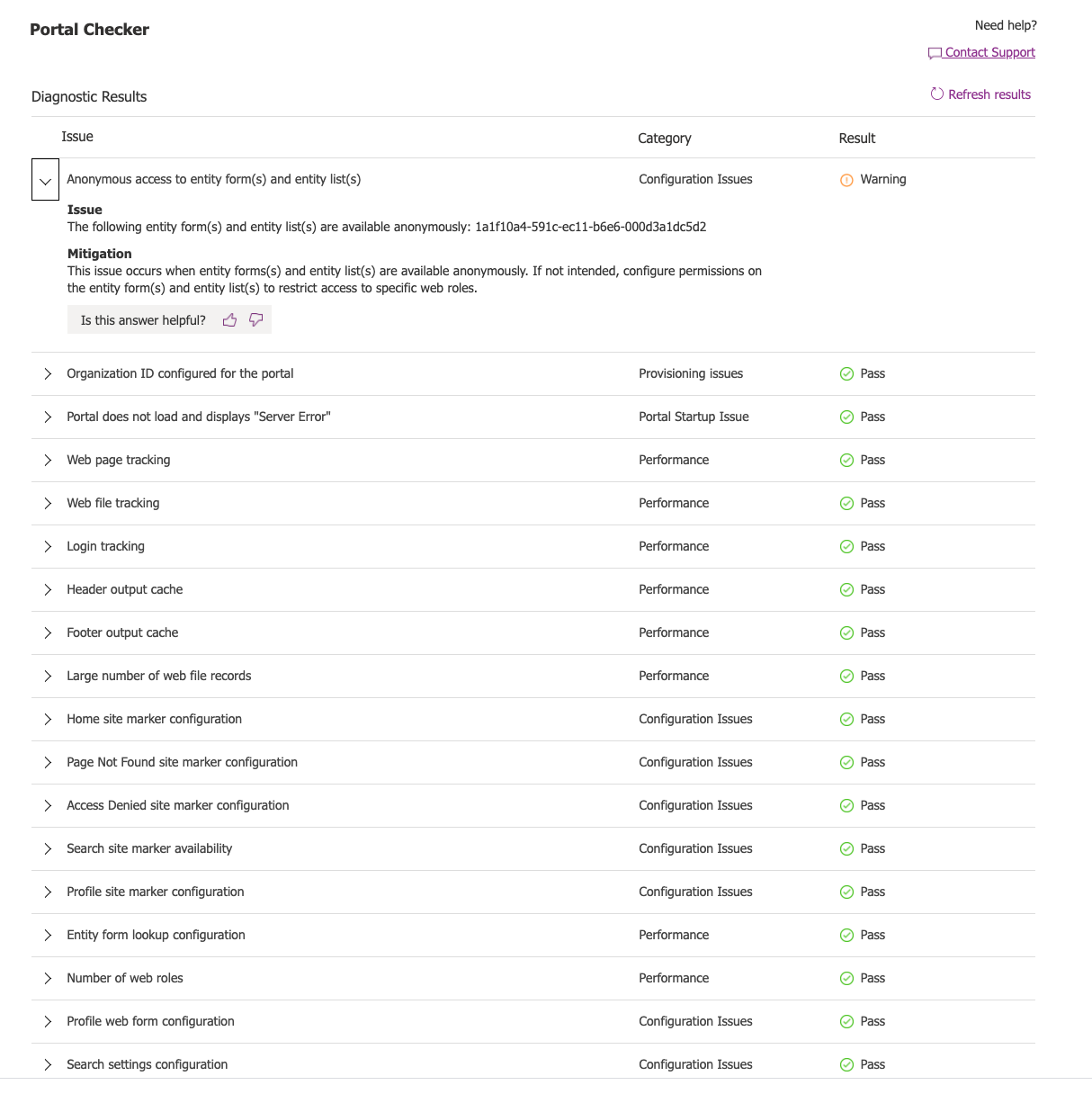
Source: Tenable Research, 2021
Get more information
- UpGuard Blog Post about Microsoft Power Apps Data Exposure
- IBM X-Force Cloud Security Threat Landscape Report for Q2 2020 through Q2 2021
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable, the first Cyber Exposure platform for holistic management of your modern attack surface.
Get a free 30-day trial of Tenable.io Vulnerability Management.
Related Articles
- Tenable.io Web Application Scanning
- Vulnerability Management








