How Solid is Your Security Framework Foundation?

A recent study from Dimensional Research, sponsored by Tenable and the Center for Internet Security, titled, “Cybersecurity Frameworks and Foundational Security Controls,” revealed that 95 percent of organizations face technological and business challenges when implementing leading security frameworks: the NIST Framework for Improving Critical Infrastructure Cybersecurity, ISO 27001/27002, CIS Critical Security Controls, and PCI.
95% of global organizations face impediments when implementing security frameworks
The study tallied survey responses from more than 300 U.S. and European IT security decision makers. Respondents from organizations of all sizes across key industries were polled to better understand the adoption and maturity of cybersecurity frameworks and their underlying security controls.
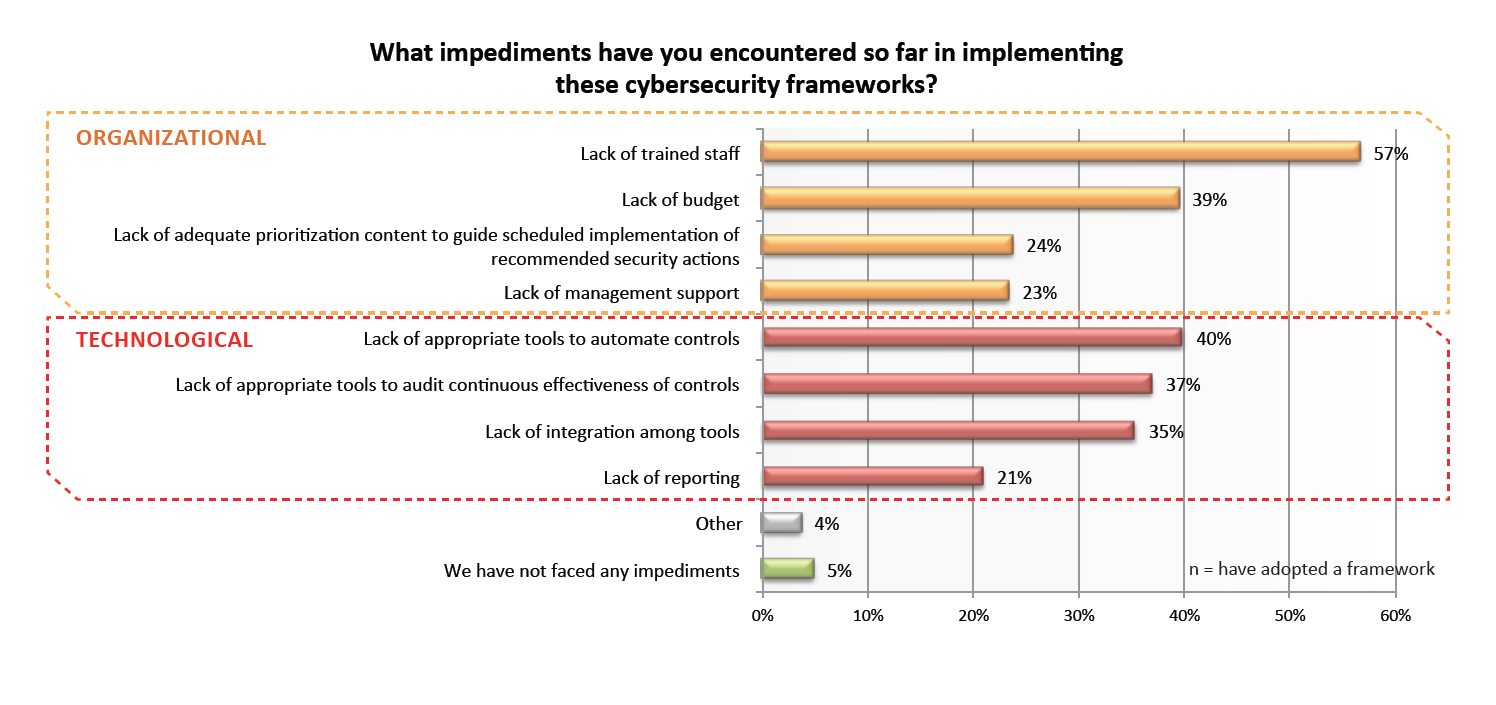
According to survey data, respondents cited shortages in trained staff (57 percent), a lack of necessary tools to automate controls (40 percent) and inadequate budget (39 percent) as the top three challenges in cybersecurity framework adoption. Other factors noted as inhibiting the successful implementation of security controls included lack of prioritization, support from management and reporting capabilities.
A focus on foundational controls
The research drilled into adoption of the five controls designated by the CIS as Foundational Cyber Hygiene. These foundational controls, a subset of the 20 CIS Critical Security Controls for Effective Cyber Defense, are an integral part of virtually all security frameworks, including the NIST Cybersecurity Framework and ISO 27001/27002. On average, only about 50% of organizations have implemented the foundational controls and related sub-controls:
- Inventory of Authorized and Unauthorized Devices
- Inventory of Authorized and Unauthorized Software
- Secure Configurations for Hardware and Software on Mobile Devices, Laptops, Workstations, and Servers
- Continuous Vulnerability Assessment and Remediation
- Controlled Use of Administrative Privileges
Only 6% of surveyed organizations have implemented the 5 foundational CIS controls
The lack of adoption can be partially explained by timing. More than half of the organizations polled have been on their control adoption journey for one year or less. Even so, it is somewhat surprising and disconcerting that only six percent of surveyed organizations have thoroughly implemented the five foundational controls. Lacking these controls organizations cannot help but struggle with preventing, detecting and responding to cyber threats and vulnerabilities.
How do you stack up?
Take our mini survey to see how your control status compares to similar sized organizations.
Get expert advice
To help you realize the benefits of adopting the foundational CIS controls, join Tony Sager, Senior VP and Chief Evangelist with CIS, and me at 2 p.m. ET on January 18, 2017 for Achieving Effective Cyber Hygiene with Critical Controls 1-5. This webinar will cover the following topics:
- Brief review of the latest survey findings on foundational control adoption
- Quantitative and qualitative benefits of foundational control adoption
- Adoption barriers and best-practices for SMB, mid-market and enterprise organization
- Advice for front line infosec practitioners and leaders
- Answers to your specific questions during a live Q&A
Please join us for this opportunity to hear and learn from a leading expert. Your questions and comments are welcome. We look forward to your participation.
Related Articles
- Announcements
- Center for Internet Security (CIS)
- Security Frameworks
- Webinars